Machine and Human Analysis Techniques (and Intelligence Cycle)
Analysis Techniques
Strategic Intelligence Analysis
In order to understand how to analyze information we must first understand the information hierarchy also known as the Data, Information, Knowledge, and Wisdom pyramid.
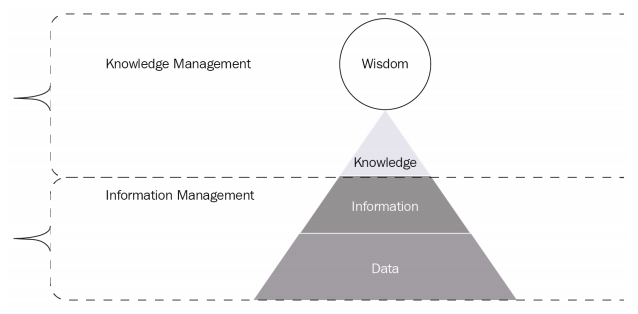
This pyramid is a graphical representation of how data is transformed into wisdom:
- The Data and Information levels are located within the Information Management section because we will need to gather data based on the Priority Information Requirements
- This data needs to be managed so that we can filter out the unnecessary pieces to obtain information
- After all of the information has been analyzed, it can then be moved and maintained in the Knowledge Management section
- From all of the information that has been gathered, the intelligence that has been developed will support the commander in making a decision
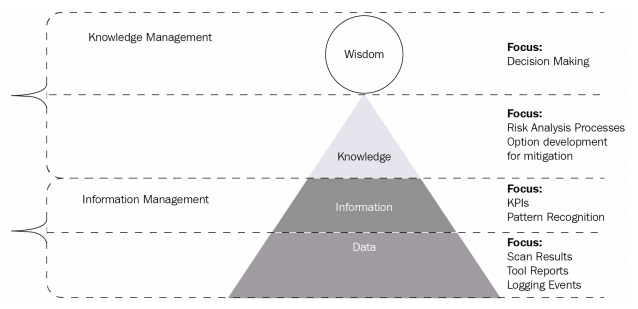
- The Data level, we will begin by gathering information from the security tools that we implement within the environment.
- At the Information level, we will filter out information based on our PIRs. Examples can be KPIs or pattern recognition from AI or machine learning tools.
- Once the information is filtered, we can move it through our risk analysis processes and weigh what our options are.
- We will then be able to present to our stakeholders with the information necessary to make a decision.
Intelligence and Cyber Security
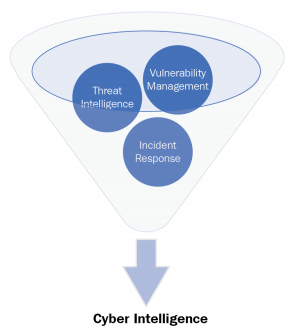
“Cyber intelligence is the ability to gain knowledge about an enterprise and its existing conditions and capabilities in order to determine the possible actions of an adversary when exploiting inherit critical vulnerabilities. It uses multiple information security disciplines (threat intelligence, vulnerability management, security configuration management, incident response, and so on) and tool sets to gather information about the network through monitoring and reporting to provide decision makers at all levels to prioritize risk mitigation.”
Military commanders make decisions based on specific pieces of data that pertain to solving a specific question. Gathering of that information for the commander is based on a term called Priority Information Requirements (PIRs). These PIRs are what drives intelligence gathering operations as it provides guidance on what information is the most important to the commander so that they can plan for the next steps.
Good PIRs have three criteria:
- They ask only one question
- They focus on a specific fact, event, or activity
- They provide intelligence required to support a single decision
Military examples:
- What size force is defending objective A?
- Will enemy battalion X arrive before Y time on Z date?
- How many obstacles are on D road that will impede our movement?
The same logic can be used within private organizations with the use of Key Performance Indicators or Key Risk Indicators. Leaders will have to provide targets, the means to measure them in order to validate whether or not they have met thresholds that are within or out of defined thresholds. Having a top-down approach when defining specific information to be derived from multiple security tools, will fuel an organization’s capability to prioritize and analyze information to be accurate, timely, and actionable.
Below are examples from the first two Center for Internet Security Controls
- Do we have an inventory of authorized and unauthorized devices?
- Tactical: Do we have a complete list of authorized devices?
- Operational: How are we continuing to gather this list?
- Tactical: Do we have the capability of identifying unauthorized devices?
- Operational: Where are we finding these devices?
- Do we have an inventory of authorized and unauthorized software?
- Operational: Where are these located?
- Operational: What security tools are in place to ensure that the information does not get compromised?
- Operational: Where do the systems with this software exist?
- Tactical: Do we have a list of authorized software?
- Tactical: What are our most critical applications?
- Tactical: How are we protecting these?
- Tactical: Do we have a list of unauthorized software?
The above scenarios provided multiple points of intelligence gathering to provide a holistic view of an organization’s risk exposure and propensity to exploited by adversaries.
The Defense Acquisition Guidebook (DAG), Chapter 7, provides guidance to Program Managers (PMs) on how to use intelligence information and data to ensure maximum warfighting capability at a minimum risk to cost and schedule.
“The ‘intelligence cycle’ is a process which forms the basis of operations in government organizations like the CIA and the NSA. It very broadly outlines the stages of developing raw information into finished intelligence for policy makers to use in decision making.”
The Intelligence Cycle
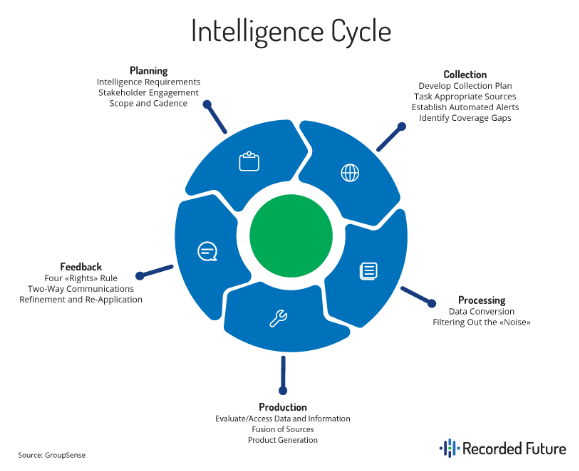
- Planning and Direction
- This category includes the receipt, identification, and prioritization of intelligence requirements; the development of concepts of intelligence operations and architectures; tasking appropriate intelligence elements for the collection of information or the production of finished intelligence; and submitting requests for collection, exploitation, or all-source production support to external, supporting intelligence entities.
- Collection
- Collection includes those activities related to the acquisition of data needed to satisfy specified requirements. This is managed by collection managers, whose duties include selecting the most-appropriate, available asset(s) and associated processing, exploitation, and dissemination (PED) and then tasking selected asset(s) and associated PED to conduct collection missions.
- Processing and Exploitation
- Data initially received from the sensor arrives in various forms, depending on the nature of the sensing device. Depending on the source, the raw input may be in the form of digitized data, unintelligible voice transmissions, or large digital files containing un-rectified images of the Earth. This collection output is converted by sensor-specific processing measures into visual, auditory, or textual information that is intelligible to humans, and can then be used by intelligence analysts and other consumers. The data conversion may be automated using algorithmic fusion, cuing, data analytics, and automated exploitation. Exploitation entails the further translation and contextualizing of information resulting from collection and initial processing into a product the planner, decision-maker, or intelligence analyst can assimilate cognitively.
- Analysis and Production
- During analysis and production, intelligence is produced from the information gathered by collection capabilities, and from the refinement and compilation of intelligence received from external organizations. All available processed information is integrated, evaluated, analyzed, and interpreted to create products that will satisfy requesters or users.
- Dissemination and Feedback
- The Right Format: Choose to present your intelligence in a format that your stakeholders can consume and understand. For example, you may not need to include everything you discovered for decision making, so work on summarizing information.
- The Right Hands: Intelligence can only be applied when made available to the correct people. Map types of intelligence not only to job titles, but to team responsibilities.
- The Right Time:Even the most relevant intelligence can be rendered useless if it’s out of date. This means you need to balance the time it will take to produce intelligence with any action that needs to be taken.
- The Right Medium: It’s not just what you communicate, but how. Choose communication methods that will reach your relevant stakeholders the most quickly and effectively.
- This category involves the timely distribution of critical information and finished intelligence, readily accessible by the user, to the appropriate consumer. The movement toward a net-centric environment has reduced the technical challenges related to information dissemination. Nevertheless, intelligence infrastructure (such as intelligence networks, systems, and software) and intelligence resources
Technical Intelligence analysis
Technical intelligence need to be accurate, timely, and actionable. Analysis methodologies are designed to provide with better ways to operationalize technical data in support of security operations.
Intelligence at this level is focused mostly on indicators of compromise (IOCs) and signatures.1
The analysis phase of the threat intelligence lifecycle aims at evaluating, analyzing and interpreting the processed information against the program’s requirements (planning phase) to provide analytic judgments that determine confidence, relevance and threat impact of the collected data.
Structured Human Analysis Techniques
CONTENT UNDER DEVELOPMENT
Direction, Collection, Processing, Analysis, Dissemination, Feedback (Review)
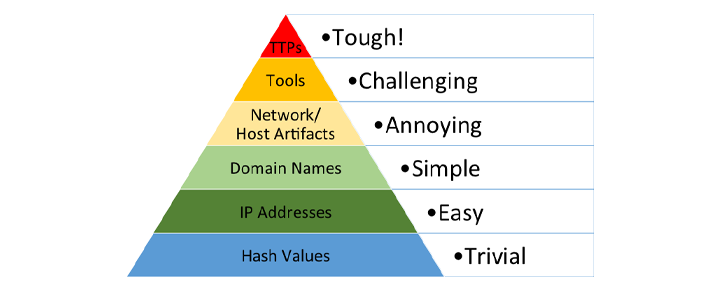
Collecting threat data is the first step in producing threat intelligence.
It is fundamental to highlight the difference between indicators and signatures as well as the difference between atomic and composite indicators.
A signature should be thought of as a fingerprint (something that have a high confidence) whereas indicators are not as precise and need to be further analyzed and contextualized to produce valuable information.
As a result of analyzing indicators we try to move from atomic indicators (a piece of information e.g. an ip) to composite indicators (putting atomic information together).
Composite information is much richer in content and can better support security operations.
The data collected is going to be as good as the use that you have of it and the analysis phase helps assessing how relevant it is to your environment.
Moving from atomic to composite indicators to climb the pyramid of pain.2
Data preparation steps
Def: Data Preparation is the process of (collecting), cleaning, and consolidating data into one file or data table, primarily for use in analysis.
-
Data consolidation refers to the collection and integration of data from multiple sources into a single destination. During this process, different data sources are put together, or consolidated, into a single data store.<br/ >
Adding more context to the atomic data to leverage pivoting points for aggregation, correlation and visualization capabilities.<br/ >
Sources for network atomic indicators enrichment:
- pDNS (A, AAAA, PTR... records)
- AS
- ASN
- Geolocation data
- BGP lookups
- …
Enriched technical indicators’ keys:
Standards#AtomicNetworkIndicators
-
Data cleansing:
Data cleansing or data cleaning is the process of detecting and correcting (or removing) corrupt or inaccurate records from a record set, table, or database and refers to identifying incomplete, incorrect, inaccurate or irrelevant parts of the data and then replacing, modifying, or deleting the dirty or coarse data.(wiki)
Removing well-known indicators that can be associated to potential false positives, errors or mistakes.
MISP offers a list of 31 sources for data cleansing.3
.
ref:
- Practical Cyber Intelligence ^
- Intelligence Support and Acquisition ^
- Applying Government Intelligence Strategies to Commercial Organizations ^






