- GB
5 years in adversary emulation
 James ChappellJames Chappell (Digital Shadows, GB)
James ChappellJames Chappell (Digital Shadows, GB)
James is the Founder and Chief Innovation officer at Digital Shadows and one of the authors of the Bank of England's standards for threat led penetration testing standards CBEST. He is a member of BCS, IISP, CREST and one of the chairs of the FIRST Cyber Threat Intelligence SIG.
5 years ago I was asked to participate in a pilot study organised by the bank of England to explore how threat intelligence could be used in a security test. What followed was a fascinating journey collaborating with penetration testing companies, professional bodies, other threat intelligence companies and financial institutions seeking to understand the effectiveness of threat led security testing. Today these standards exist as CBEST, TIBER-EU and Asian regulatory testing frameworks.
The pilot programmes were created in collaboration with institutions to respond to criticism of the sector not taking the results of red team exercises seriously and viewing them as compliance driven exercises. Similarly, testing teams were following well trodden paths, but sometimes without justification for why the particular testing path had been chosen. Businesses also sometimes struggled to justify the investment required to address the findings without really understanding how likely a risk would be to come to pass.
This talk explores what went well, the opportunities for improvement and how that market has evolved since. We also look to the future of the discipline with MITRE recently introducing the concept of adversary emulation profiles as part of the work on ATT&CK, this talk also explores the opportunities this creates in threat led security testing and vulnerability management and how related disciplines .
Participants will learn:
- An understanding of how adversary emulation is applied in red team security tests.
- Lessons learned from practical experience in Threat Led Penetration Testing: the good, the bad, the ugly.
- How to apply Cyber Threat Intelligence to a security test.
- Where CTI for adversary emulation in testing is heading.
- Why teams should be purple.
March 19, 2019 13:00-13:30
james-cha.pdf
MD5: 1e3daa2bb0797166f4fcb85d4e02f344
Format: application/pdf
Last Update: June 7th, 2024
Size: 20.78 Mb
- GR
5 years of applied CTI discipline: where should organisations put focus on?
 Andreas SfakianakisAndreas Sfakianakis (Royal Dutch Shell, GR)
Andreas SfakianakisAndreas Sfakianakis (Royal Dutch Shell, GR)
Andreas Sfakianakis is a Cyber Threat Intelligence and Incident Response professional. Andreas is currently a CTI Analyst of Royal Dutch Shell based in Netherlands. He is also a member of European Network and Information Security Agency’s Threat Landscape Stakeholders’ Group and an external expert for ENISA and European Commission. He is a former CTI Analyst at Lloyds Banking Group and Network Information Security Expert at ENISA. He has more than 5 years of experience on Cyber Threat Intelligence field working and engaging with organizations from the banking and Oil & Gas sectors, European agencies, CERTs/CSIRTs, law-enforcement, intelligence professionals and researchers.
Andreas has been the co-author of a number of reports, namely: WEF's Global Risks 2013: "Digital Wildfires in a Hyperconnected World", ENISA's Threat Landscape 2012, ENISA's report on "Exploring the opportunities and limitations of current Threat Intelligence Platforms". He has also participated in the reviewing of ENISA CERT exercises as well as in various research and innovation proposals for European Commission. Finally, Andreas has been the Editor-in-chief of the "Threat Intel Weekend Reads" newsletter for 3 years.
Andreas' Twitter handle is @asfakian!
Since the publication of Mandiant’s APT1 report in 2013, cyber threat intelligence discipline has been widely adopted by organisations globally. We have observed success stories as well as fails of organisations trying to develop CTI capabilities or, in other words, adding value to business. As a community, it is critical to capture the relevant lessons learned and conduct a status check for these 5 years of applied CTI discipline.
The utmost goal of this presentation is to identify the areas that organisations should put more focus on. Based on our assessment, we identify and deep dive into the three major areas where most current CTI teams struggle: 1) intelligence direction (such as stakeholder identification and collection of intelligence requirements), 2) intelligence reporting and dissemination and 3) CTI analyst's skill set.
Key takeaways of this presentation include:
- the realization of the significance of intelligence requirements for the intelligence cycle
- how proper stakeholder identification increase situational awareness
- how classic intelligence approaches can be applied to CTI production
- success stories on disseminating intelligence products and capturing feedback
- understanding the variety of competencies of CTI teams and ways of baselining analysis process within CTI teams.
March 19, 2019 09:00-09:30
- JP
A Lightweight Markup Language for Graph-Structured Threat Sharing
 Mayo YamasakiMayo Yamasaki (NTT-CERT, JP)
Mayo YamasakiMayo Yamasaki (NTT-CERT, JP)
Mayo Yamasaki is a researcher at NTT Secure Platform Laboratories and also a member of NTT-CERT in Japan since 2015. He studied information science and natural language processing at NAIST (Nara Institute of Science and Technology). Since he joined NTT he’s been researching and developing software systems for cybersecurity-related information extraction and retrieval with machine learning.
Sharing of structured threat intelligence is essential to address increasing and complicating cyberattacks. However, 60% of practitioners use unstructured data expression in daily operations because existing structured expressions designed for inter-system communications are complex to describe. To tackle this problem, NTT-CERT is developing a lightweight markup language for graph-structured threat intelligence that is easy for both humans and machines to read and write like Markdown. In this talk, first, I introduce a novel lightweight markup language which can easily describe STIX 2.0 compatible graph data with an editing cost of 2 compared with JSON format STIX and 19% compared with the DOT language. By integrating the language into existing threat intelligence platforms as a new interface, creating and enriching intelligence become more efficient. Second, I experimentally demonstrate capabilities and limitations of the proposed language. Finally, I also demonstrate a system to create threat intelligence by using the proposed language with practical examples.
March 19, 2019 17:30-18:00
- NL
A Place for Analysis of Competing Hypothesis (ACH) in CTI: Applications and Evolution of ACH in CTI
 Caitlin HueyCaitlin Huey (EclecticIQ, NL)
Caitlin HueyCaitlin Huey (EclecticIQ, NL)
Caitlin Huey is a Senior Threat Intelligence analyst at EclecticIQ Fusion Center. She has been working as an analyst since 2013 and has been involved in various information sharing communities. Prior to that, Caitlin received her Master’s in Security and Intelligence Studies at the University of Pittsburgh.
Within the intelligence community, analyst tradecraft is referred to as a method or a portfolio of known structured techniques, methods, and skills that aid an analyst in doing their job. Analysis of Competing Hypotheses (ACH) is commonly cited as a method used to evaluate hypotheses against a set of evidence. Analysts operating over several “INTs” have relied on a way to effectively test data coming from multiple sources and producers in order to measure evidence against them. During the course of an investigation, analysts may need to evaluate what is consistent and inconsistent across a set of hypotheses (H1, H2, H3). ACH improves an analyst’s ability to assess and validate an issue with a tested confidence assertion. In CTI, producers and consumers of cyber threat intelligence have largely relied on ACH to evaluate data and analyze it on the basis of identifying attribution, patterns, motivations, and more. As ACH in CTI is evolving, it is leading analysts to find innovative ways to represent and structure this process so that it is scalable to produce and consume.
Audience takeaways include:
- Analysis of Competing Hypothesis (ACH) has been done and is still being done by analysts operating in the private and public spheres. Not only has it been done in traditional intelligence communities, but has also been conducted by cyber threat intelligence (CTI) vendors who use ACH to evaluate an incident/emerging threat.
- Learn how ACH has been used and how to apply it to the current threat landscape.
- Understand ACH as a method used to allow producers/vendors of threat intelligence to map and structure a higher confidence in one hypothesis (H1) over a tested set of other hypotheses (H2, H3, H4).
- See how and when producers conduct ACH, it gives consumers of threat intelligence a more complete picture of an emerging threat. It also enables a consumer to see the evidence weighed against each Hypothesis and to come to a more informed decision based on the evidence available to them.
- Evolution of ACH in CTI - see how analysts can better represent this tradecraft by applying structure to the ACH process
March 20, 2019 14:00-14:30
- US GB
Adventures in Blunderland
 Allison WikoffAllison Wikoff (Secureworks, US), Matt Webster (Secureworks, GB)
Allison WikoffAllison Wikoff (Secureworks, US), Matt Webster (Secureworks, GB)
In this session join Allison Wikoff and Matt Webster, both Senior Threat Researchers from Secureworks’ Counter Threat Unit, as they journey down the rabbit hole to explore a world of threat actor mistakes. The session will uncover some of the weird and wonderful errors adversaries are making across the criminal and targeted threat landscapes, and will ultimately show that threat actors are human too. During this session Allison and Matt will demonstrate how network defenders and security researchers have been able to capitalize on these mistake to understand and more effectively defend against a wide-range of threat actors when they slip up.
March 19, 2019 13:30-14:00
- US
All Your Heatmap Are Belong To Us - Building an Adversary Behavior Sighting Ecosystem
 Richard StruseRichard Struse (MITRE, US)
Richard StruseRichard Struse (MITRE, US)
Richard Struse is the Chief Strategist for Cyber Threat Intelligence (CTI) at The MITRE Corporation, leading the effort to improve cyber defense by better understanding the adversary’s tactics and techniques. In addition, he is the chair of the Cyber Threat Intelligence Technical Committee within OASIS, an international standards development organization. In 2018, Mr. Struse was elected to serve on the board of directors of OASIS. Previously, Mr. Struse served as the Chief Advanced Technology Officer for the U.S. Department of Homeland Security’s National Cybersecurity and Communications Integration Center (NCCIC) where he was responsible for technology vision, strategy and implementation in support of the NCCIC’s mission. Mr. Struse is the creator of the STIX and TAXII automated information sharing initiatives which have been widely adopted across the public and private sectors. In October 2014, Secretary of Homeland Security Jeh Johnson presented Mr. Struse with one of the department’s highest honors, the Secretary’s Award for Excellence, in recognition of his pioneering work on STIX and TAXII. Prior to joining DHS, Mr. Struse was Vice President of Research and Development at VOXEM, Inc., where he was responsible for the architecture, design and development of a high-performance, extreme high- reliability communications software platform that is in use in telecommunications systems around the world. He began his technical career at Bell Laboratories where his work focused on tools to automate software development and the UNIX operating system. In 2015 Mr. Struse was named by Federal Computer Week as one of the “Federal 100” in recognition of his leadership role in the development of cyber threat intelligence technology standards. In 2016, OASIS selected Mr. Struse to receive their “Distinguished Contributor” award for his work as “a pioneer in the development of the STIX, TAXII, and CybOX standards and was instrumental in successfully transitioning the CTI work to OASIS.”
March 19, 2019 14:00-14:30
- GB
 Richard GoldRichard Gold (Digital Shadows, GB)
Richard GoldRichard Gold (Digital Shadows, GB)
Richard Gold is an information security professional experienced in both offensive and defensive security, as well as security engineering. He has worked for Cisco on web proxies and Secure Development Lifecycles (SDLs), AGT International on Internet of Things/SCADA and, currently, Digital Shadows as Director of Security Engineering. He is particularly interested in open source intelligence (OSINT) reconnaissance, Advanced Persistent Threat (APT) campaigns, and offensive security techniques. He is a Certified SCADA Security Architect and holds a PhD in Computer Networking.
Building effective and appropriate threat models for your organization isn’t easy. At its most basic level, threat modelling is a way of structuring thinking around what critical assets an organization has, and which are the likely threats to that organization. However, a company’s own measure of criticality may not match the thought process of an attacker, which means that it can be tricky to understand what constitutes a “critical asset”. Likewise, comprehending what an attacker wants might not be immediately obvious as your organization may only be appealing as a stepping stone in a much larger operation.
This is where MITRE’s PRE-ATT&CK framework comes into its own. Digital Shadows draws on its analysis of US Department of Justice (DOJ) indictments and its collaboration with the MITRE corporation to demonstrate why organizations need to update their threat models now. This session will show how sophisticated adversaries use the files and output of one intrusion (ATT&CK) as reconnaissance for their next attack (PRE-ATT&CK); in other words, ATT&CK often refers to the PRE-ATT&CK phase of a much larger operation. You may assume that your organization is of no interest to a large criminal outfit or sophisticated adversary, but in reality, these attackers may use you as a crucial pivot point to achieve their loftier objectives.
Outlining campaigns in this way has several advantages for defenders. It provides a useful way to identify an adversary’s goals, allowing you to focus on improving the areas most relevant to the risks you face. Using PRE-ATT&CK will also help you determine appropriate mitigation steps for each distinct phase of an attack, based on the actual tactics and techniques being used by threat actors today.
Attendees will learn:
- How to use public indictments to map real-world campaigns against MITRE ATT&CK and PRE-ATT&CK
- How to identify an adversary’s goals and relevant mitigation by using the PRE-ATT&CK framework
- Why you should update your threat model as you may be used as a pivot-point in a broader campaign
March 20, 2019 09:30-10:00
rich-gold.pdf
MD5: 1c536c261e9a707e64faecff3edd5124
Format: application/pdf
Last Update: June 7th, 2024
Size: 4.81 Mb
- US
Beginner Tracking Adversary Infrastructure
 Michael SchwartzMichael Schwartz (Target, US), Tim Helming (DomainTools, US)
Michael SchwartzMichael Schwartz (Target, US), Tim Helming (DomainTools, US)
Michael has nearly 20 years of experience in nearly all aspects of IT and then some. He began his career working Help Desk through High School and College and eventually turned that knowledge into his first full-time position with McKinley Associates in Ann Arbor, MI as a Support Specialist. Later he worked as a Systems Engineer and Field Support Engineer for government contractors. Michael eventually landed his dream job with the FBI as an Intelligence Analyst where he was involved in Counterterrorism and Cybersecurity matters. Michael returned to the public sector with Lookout as an Android malware reverse engineer and figures he has finally settled down in Minneapolis, MN with Target as the Director of Threat Intelligence Detection Engineering. Michael holds a BA in Political Science from the University of Michigan, an MS in Defense and Strategic Studies from Missouri State, and an MS in Computer Science of the University of Illinois – Springfield.
Virtually every organisation’s network is targeted at one time or another--in some cases continuously--by threat actors seeking to gain privileged access to protected resources. Many of the stages of an attack, as described in popular frameworks such as the Cyber Kill Chain or MITRE’s ATT&CK, depend on various kinds of infrastructure controlled by the adversary. Blue teams, however, often see only a small glimpse of this infrastructure, and in some cases only see it after much damage has been done. Moreover, threat intelligence feeds almost always have blind spots which prevent network defenders from seeing the components of the attack network.
However, more and more organisations are learning the value of profiling and mapping adversaries through analysis of connected infrastructure. This analysis helps blue teams shift their focus to earlier stages of attacks, which in turn can often thwart a campaign before it can cause damage.
In this workshop, presenters Mike Schwartz (Target Corporation) and Tim Helming (DomainTools) will teach key methods of infrastructure analysis, moving from concept to real-world case study to hands-on training.
Part 1 of the workshop will encompass the following stages and concepts:
- Description of the problem space: Gaps we are seeing in threat intelligence coverage--what the threat feeds miss (and why it isn’t their fault)
- Basic adversary investigation concepts including how to enumerate and map attack infrastructure, and more importantly, how to use that data to inform your security posture
- Tools of the trade: a review of various open-source and commercial tools, what each offers, and how to use them in concert with one another
- Resource considerations including how to make the most of a limited budget, and how to set the stage today for success tomorrow
- Walkthrough of several actual historical cases, describing how the scenario and subsequent investigation--and defence--unfolded
Part 2 is devoted to hands-on training. Attendees will split into small groups and work cooperatively on exercises specifically developed for this workshop.
- Scenario-based exercises present the team with a set of data, from which they are expected to develop a more complete picture of the incipient attack
- Each team will present their findings to the other teams
- The presenters will give feedback on the exercises, both along the way as well as in a concluding section at the end of the workshop.
March 18, 2019 09:00-13:00, March 18, 2019 14:00-18:00
- NO
Bootstrapping a Threat Intelligence Operation
Jon Røgeberg (mnemonic, NO)
Jon Røgeberg works as the Manager for mnemonic’s Threat Intelligence team. He is also the Operational Manager of mnemonic IRT and responsible for Forensics in mnemonic. He has been responsible for building mnemonic’s Threat Intel Team since 2011 and has more than 10 years’ experience with Incident Response ranging from virus outbreaks, opportunistic crime, targeted crime and advanced targeted attacks.
In this presentation, Jon will share experiences from himself and his team, from jumpstarting and increasing maturity of threat intel operations. He will cover observations and lessons learned, and share examples of what have worked. The intended audience is anyone who advises and consults different threat intel teams and members and stakeholders of smaller threat intelligence operations.
March 19, 2019 09:30-10:00
- US
Building, Running, and Maintaining a CTI Program
 Michael J. Schwartz
Michael J. Schwartz Ryan MillerMichael J. Schwartz (Target, US), Ryan Miller (Target Corporation )
Ryan MillerMichael J. Schwartz (Target, US), Ryan Miller (Target Corporation )
Michael has nearly 20 years of experience in nearly all aspects of IT and then some. He began his career working Help Desk through High School and College and eventually turned that knowledge into his first full-time position with McKinley Associates in Ann Arbor, MI as a Support Specialist. Later he worked as a Systems Engineer and Field Support Engineer for government contractors. Michael eventually landed his dream job with the FBI as an Intelligence Analyst where he was involved in Counterterrorism and Cybersecurity matters. Michael returned to the public sector with Lookout as an Android malware reverse engineer and figures he has finally settled down in Minneapolis, MN with Target as the Director of Threat Intelligence Detection Engineering. Michael holds a BA in Political Science from the University of Michigan, an MS in Defense and Strategic Studies from Missouri State, and an MS in Computer Science of the University of Illinois – Springfield.
Ryan is a Cyber Intelligence Manager with over 16 years of operational intelligence experience in commercial, military and US government environments. Currently working at Target Corporation managing an intel team providing strategic and operational analysis, proactively tracking cyber threat actors’ capabilities, methodologies and tactics and operations. Ryan also has industry experience with developing and advancing cyber threat intelligence programs - including strategy, operations, processes and capabilities. Plus, he knows Kyle Davis.
Learn the nuts and bolts from the Target CTI program managers. Ryan and Michael have been building, running, and maintaining their CTI program for the last three years and they're here to share a wealth of information on what's worked right, and what's gone horribly wrong. Need to start a program? Need to find a way to measure the performance of your CTI program? Want to avoid some common pitfalls that plague the CTI industry? Then you have no choice to attend because we'll put it all on the line for you.
March 19, 2019 10:00-10:45
- US
Building STINGAR to enable large scale data sharing in near real-time
 Jesse BowlingJesse Bowling (Duke University, US)
Jesse BowlingJesse Bowling (Duke University, US)
Jesse Bowling is the Security Architect and CSIRT Program Manager for Duke University. He has spent over 20 years on staff at academic institutions, public and private, large and small. Professionally, his interests lie primarily in detection and response. In his personal time, Jesse enjoys cooking, spending time with his family, and grumbling nearly inaudibly as he wanders behind his family, turning off lights throughout the house.
Duke University has embarked on a multi-year mission to help lower the difficulty on automated threat intelligence sharing across higher education institutions under the umbrella project STINGAR (Shared Threat Intelligence for Network Gatekeeping and Automated Response). The overarching goals of STINGAR are to enable organizations (especially higher education) across a wide range of technical, operational maturity, and budget resources to collect, analyze, action, and share threat intelligence.
Duke began moving to an “active defense” or “automated response” model for blocking attackers in 2014. Around this same time, we began exploring the use of honeypots for detecting attackers, and found that honeypots provided a very effective way to identify external attackers of common services quickly with low false positive rates. We quickly realized that the data we generated locally could easily be shared to others, and we began making our data available to other schools and organizations.
Based on our experiences, Duke created the STINGAR project with the goals of:
- Simple, low-friction deployment of intelligence collection sensors (honeypots initially)
- Central collection of intelligence from sensors and outside sources, for analysis
- Simple methods for sharing data to peers
- A variety of methods and guidance for feeding threat intelligence to protection devices
In this presentation we will provide additional background and details on Duke’s experiences with integrating threat intelligence into the overall security program, discuss existing and future features of the CHN system, models of data sharing, and evaluation methods and metrics on effectiveness. We hope to encourage discussion around the general approach, as well as discussions on how others are generating and using threat intelligence, with the hope of identifying new ways that the data we’re collecting can be shared with the community for the benefit of defenders.
March 20, 2019 17:30-18:00
1730-1800-Building-STINGAR-Bowling.pptx
MD5: 5cb11f3a14d683fd5115c50dda5a3d2f
Format: application/vnd.openxmlformats-officedocument.presentationml.presentation
Last Update: June 7th, 2024
Size: 5.92 Mb
- US
Cloudy with low confidence of Threat Intelligence: How to use and create Threat Intelligence in an Office365 Environment
 Dave HerraldDave Herrald (Splunk, US), Ryan Kovar (Splunk, US)
Dave HerraldDave Herrald (Splunk, US), Ryan Kovar (Splunk, US)
Dave is a technical information security professional currently working as a staff security strategist for Splunk. He’s currently focused on the Splunk Boss of the SOC(BOTS), performing research into adversary simulation for blue teams, training technical security teams around the globe, and helping Splunk customers implement advanced security use cases. Dave has worked in various information security roles including pre-sales engineer, strategic security consultant, penetration tester, hands-on security architect/engineer/analyst, and chief information security officer. He’s a regular speaker at Information Security conferences and holds a number of security certifications including GIAC Security Expert (GSE) #79.
Ryan Kovar fought in the cyberwars and has been doing cybery things for almost 20 years. Now he is a Principal Security Strategist at Splunk building cool stuff, talking about security thingies, and helping other people fight their battles. He hates printers.
Is your organization using cloud email or considering migrating to the cloud? Chances are the answer to that question is yes! Your end users, IT admins, and management stand to benefit from the benefits and cost savings that cloud email brings with it. However, whether you know it yet not, this move will very likely introduce a rather large blind spot into your security visibility. Capabilities that security analysts and incident responders have come to depend on in their on-prem solutions often work very differently or are gone altogether, in popular cloud email offerings. In this talk, we will describe the current state of cloud email visibility for security teams and offer practical, hands-on solutions for Microsoft Office 365 utilizing open source tools like (stoQ and LAIKAboss) to regain visibility to email headers and analyze attachments.
March 19, 2019 16:00-16:30
- US
Shaul Holtzman (Intezer, US)
Genetic Malware Analysis leverages binary code reuse in order to automate malware analysis and accelerate incident response. Intezer’s technology tracks the evolution of software and provides a platform that empowers existing sensors with unique capabilities. Learn how Genetic Malware Analysis can be used at every level of incident response, from detection to containment and remediation.
March 20, 2019 16:30-17:00
- GB
Drawing the line: cyber mercenary or cyber threat intelligence provider?
Stewart Bertram (Elemendar, GB)
The last decade has seen the world of cyber security change beyond all recognition, from an adjunct consideration within the IT department to a global level security concern. Wikileaks, Stuxnet, Sony, APT1 and Notpetya are just some of the keywords associated with incidents that have heralded the increased securitisation around the issue of 'cyber' and how it has become a critical issue for many invested in security. Within this context, actors such as governments have obviously had to reconsider their attitude towards cyber security. However, how has the role of the cyber threat intelligence (CTI) provider changed over the last decade?
As the context of CTI changes, and security services become politicised by implication, so the role of a CTI provider changes - from IT professional to potential cyber mercenary. This talk considers how the context of cyber security has changed and how this may affect CTI providers over the next decade.
March 19, 2019 16:30-17:00
- NL
EVALUATE OR DIE TRYING - A Methodology for Qualitative Evaluation of Cyber Threat Intelligence Feeds
 Sergey Polzunov
Sergey Polzunov Jörg AbrahamSergey Polzunov (EclecticIQ, NL), Jörg Abraham (EclecticIQ, NL)
Jörg AbrahamSergey Polzunov (EclecticIQ, NL), Jörg Abraham (EclecticIQ, NL)
Mr. Sergey Polzunov is a Senior Software Engineer in the EclecticIQ Fusion Center. He is responsible for prototyping analyst-centric tools and for technical support of the Fusion Center Threat Intelligence Platform. He is the author of OpenTAXII and has more than 10 years of software development experience.
Mr. Jörg Abraham is a Senior Threat Intelligence Analyst in the EclecticIQ Fusion Center. He is responsible for analyzing Cyber Threats and providing accurate, timely and structured intelligence relevant to EclecticIQ's customers. Before joining EclecticIQ he has been working for Royal Dutch Shell for more than 10 years in various Cyber Defense positions. Mr. Jörg Abraham is a Certified Information System Security professional (CISSP) and GIAC Certified Forensic Analyst (GCFA).
CTI as a practice is getting more traction in recent years. Organizations begin to understand how threat intelligence plays in context with their existing security operations.
At the same time, they face difficulties to judge the quality of sources, eventually failing to assess the return on investments.
In this talk, Sergey Polzunov and Jörg Abraham will present how organizations can evaluate the quality of an intelligence source and how structured intelligence aids in making a qualitative statement about the value of an intelligence feed.
The talk will conclude with a PoC demonstrating feed assessment in an automated way.
Attendees will learn:
- About a methodology to relate information from an intelligence source back to the intelligence requirements.
- How to measure the feed quality in an automated way.
- Why structured threat intelligence (STIX) plays an important role in feed assessment.
March 20, 2019 13:00-13:30
- US
File-Centric Analysis through the Use of Recursive Scanning Frameworks
David Zawdie (US)
David is an analyst working in private industry focusing on defending organizations against malicious threats. With over 10 years experience in information security and computer network defense, David is a passionate blue-team defender and strong advocate of open source software.
Defenders encounter a myriad of ways in which threat actors operate to deliver, exploit and install payloads in order to achieve their objective. Regardless of methods employed, the needs of an attacker frequently requires the use of an object contained in a particular file format. Analyzing various file types requires knowledge of numerous specifications and disparate tools to parse data structures. In addition, there is a need to identify interesting observations from metadata, as well as techniques and embedded objects contained inside bespoke files.
This session will provide background regarding the needs for and requirements of file-centric analysis, demonstrate the effectiveness of popular open source frameworks, and highlight opportunities for extending detection and response efforts. The discussion will include an overview of the frameworks, their approach for presenting a unified system for analysis, and details on how to actively participate in the respective open source projects through contributions that further extend capabilities via new modules and integrations.
At the conclusion of this session, attendees will be able to:
- Define the intent, purpose and scope of file-centric analysis
- List and describe capabilities from several open source recursive scanning frameworks
- Determine potential opportunities to improve existing analysis workflows
- Identify opportunities to further extend the existing frameworks by contributing to open source projects
March 20, 2019 17:00-17:30
- GB US
FIRST CTI SIG BoF
 James Chappell
James Chappell Krassimir TzvetanovJames Chappell (Digital Shadows, GB), Krassimir Tzvetanov (Purdue University, US)
Krassimir TzvetanovJames Chappell (Digital Shadows, GB), Krassimir Tzvetanov (Purdue University, US)
James is the Founder and Chief Innovation officer at Digital Shadows and one of the authors of the Bank of England's standards for threat led penetration testing standards CBEST. He is a member of BCS, IISP, CREST and one of the chairs of the FIRST Cyber Threat Intelligence SIG.
Krassimir Tzvetanov is a security engineer at Fastly, a high performance CDN designed to accelerate content delivery as well as serve as a shield against DDoS attacks.
In the past he worked for hardware vendors like Cisco and A10 focusing on threat research, DDoS mitigation features, product security and best security software development practices. Before joining Cisco, Krassimir was Dedicated Paranoid (security) at Yahoo!, Inc. where he focused on designing and securing the edge infrastructure of the production network. Part of his duties included dealing with DDoS and abuse. Before Yahoo! Krassimir worked at Google, Inc. as an SRE for two mission critical systems, the ads database supporting all incoming revenue from ads and the global authentication system which served all of the company applications.
Krassimir has established a couple of Threat Intelligence programs at past employers in the past and has been actively involved in the security community facilitating information exchange in large groups.
Currently Krassimir is a co-chair and co-founder of the FIRST CTI SIG.
Before retiring, he was a department lead for DefCon, and an organizer of the premier BayArea security event BayThreat. In the past he was also an organizer of DC650 - a local BayArea security meetup.
Krassimir holds Bachelors in Electrical Engineering (Communications) and Masters in Digital Forensics and Investigations.
March 20, 2019 15:00-18:00, March 20, 2019 11:30-12:00
- NL
Going from Guilt to Guild: Confessions of a TI Provider
 Diederik PerkDiederik Perk (Fox-IT, NL)
Diederik PerkDiederik Perk (Fox-IT, NL)
This talk explores the repercussions of public documentation of cyber threat research revealing operational details that the threat actor(s) can subsequently use to apply fixes to increase its stealth and effectiveness.
March 19, 2019 17:00-17:30
- US
 Toni GidwaniMarika Chauvin (ThreatConnect, US), Toni Gidwani (ThreatConnect, US)
Toni GidwaniMarika Chauvin (ThreatConnect, US), Toni Gidwani (ThreatConnect, US)
Toni Gidwani is the Director of Research at ThreatConnect and leads ThreatConnect’s research team, an elite group of globally-acknowledged cybersecurity experts dedicated to tracking down existing and emerging cyber threats. Her team routinely publishes research pertaining to cybercrime and nation-state attacks and actors, including a body of work surrounding Russian efforts to hack the 2016 U.S. presidential election. Toni has presented at security conferences worldwide and has appeared in many top journalistic outlets including The Economist, CNN, the Financial Times, and the New Yorker. Prior to joining ThreatConnect, Toni led analytic teams in the U.S. Department of Defense. She also teaches a graduate cybersecurity course at Georgetown University. You can follow her on Twitter @t_gidwani where she tweets about bad puns and cybersecurity.
Marika Chauvin is a Senior Threat Intelligence Researcher at ThreatConnect. Prior to ThreatConnect, Marika helped develop Chevron’s Cyber Intelligence Center, and worked as a contractor with the U.S. Department of State’s Cyber Threat Analysis Division. Marika is a non-state threat actor subject matter expert and has done extensive research focusing on hacktivist and independent hacker groups. Marika lives in New Orleans with her husband, cats, and puppy.
Many teams across the maturity spectrum struggle to show the return on investment for threat intelligence. This talk will focus on developing measures of effectiveness, independent of what tools or vendors you use. Based on multiple surveys, we’ll show where the disconnects are between threat intelligence practitioners, directors, and cybersecurity decision makers and how to focus on the most useful metrics when explaining the value of threat intelligence to your boss.
March 20, 2019 11:30-12:00
- US
Insights and Challenges to Automated Collaborative Courses of Action
 Allan Thomson
Allan Thomson Bret JordanAllan Thomson (LookingGlass, US), Bret Jordan (Symantec, US)
Bret JordanAllan Thomson (LookingGlass, US), Bret Jordan (Symantec, US)
As LookingGlass Chief Technology Officer, Allan Thomson has more than three decades of experience across network, security, and distributed systems technologies. Allan leads technical and architecture strategy across the LookingGlass solutions portfolio.
Allan is also co-chair of OASIS CTI Interoperability Sub-committee that is introducing STIXPreferred certification program for the new STIX/TAXII version 2 standards.
Prior to LookingGlass, Allan served as Principal Engineer at Cisco Systems, Inc., where he led the software architecture and design of the company’s Cyber Threat Defense System and Platform Exchange Grid. He was responsible for overall systems management and security telemetry collection/aggregation, as well as distributed threat analysis/intelligence services in multi-tenant public and private cloud deployments.
Before joining Cisco, Allan oversaw the technology growth initiatives of several start-up companies, including Airespace, where he was a Software Architect responsible for the design, development and network management/location tracking of the company’s wireless local area network (WLAN) system.
Bret Jordan is a seasoned business leader and Cybersecurity Architect with over 20 years of experience in cybersecurity. He has worked with an eclectic mix of global enterprise companies, startups, nonprofits, academic institutions. He currently works at Symantec where he heads security architecture and standards in the Office of the CTO and at Carden Memorial School as a pro bono CIO. Bret is currently serving as Chair of the TAXII subcommittee and editor of the STIX and TAXII specifications for the Cyber Threat Intelligence Technical Committee at OASIS and Co-Chair of the Implementation Considerations sub-committee for the OpenC2 Technical Committee at OASIS. Bret also contributes to several IETF working groups and to several Questions in ITU-T Study Group 17.
Today, cyber defenders typically have to manually identify and process prevention, mitigation, and remediation steps in order to protect their systems and networks and address and contain problems identified during and after an incident response.
Due to the increase and sophistication of cyber attacks from Threat Actors and Intrusion Sets the need for a secure mechanism that would enable system and network operators to respond to incidents in machine relevant time has raised significantly. While some attacks may be well known to certain security experts and cyber researchers they are often not documented in a way that would enable automated mitigation or remediation. A documented way of describing prevention, mitigation, and remediation actions is critical for cyber defenders to respond more quickly and reduce the exposure from an attack.
This talk will focus on a new technology standard that works with STIX 2.x and TAXII 2.x for creating playbooks and collaborative automated course of action operations for cyber security. This standard combines CTI with the ability to define preventive, mitigative, and remediate steps for effective deployment of security.
March 20, 2019 13:30-14:00
- GB
Logistical Budget
 Éireann LeverettÉireann Leverett (Concinnity Risks, GB)
Éireann LeverettÉireann Leverett (Concinnity Risks, GB)
Éireann Leverett once found 10,000 vulnerable industrial systems on the internet.
He then worked with Computer Emergency Response Teams around the world for cyber risk reduction.
He likes teaching the basics, and learning the obscure.
He continually studies computer science, cryptography, networks, information theory, economics, and magic history.
He is also fascinated by zero knowledge proofs, firmware and malware reverse engineering, and complicated network effects such as Braess' and Jevon's Paradoxes. He has worked in quality assurance on software that runs the electric grid, penetration testing, and academia. He likes long binwalks by the hexdumps with his friends.
Éireann Leverett is a regular speaker at computer security conferences such as FIRST, BlackHat, Defcon, Brucon, Hack.lu, RSA, and CCC; and also a regular speaker at insurance and risk conferences such as Society of Information Risk Analysts, Onshore Energy Conference, International Association of Engineering Insurers, International Risk Governance Council, and the Reinsurance Association of America. He has been featured by the BBC, The Washington Post, The Chicago Tribune, The Register, The Christian Science Monitor, Popular Mechanics, and Wired magazine.
He was part of a multidisciplinary team that built the first cyber risk models for insurance with Cambridge University Centre for Risk Studies and RMS.
Can we quantitatively compare eagles to bears or snakes to pandas? Is the infrastructure a threat group uses against us not just for qualitative study, but also for quantitative? If you ever wondered what Cryptowalls ROI compared to cryptolocker, this talk is for you!
Our development goal is to understand who burns more infrastructure against us, who has more coders, who uses more domains. We can (and do!) visually represent operational patterns and the amount of infrastructure thrown against us. When managers as you for your gut feel about different threats, why not paint them a picture with data visualisation and quantitative analysis?
https://github.com/Concinnity-Risks/LogisticalBudget
Got a MISP instance? Go home with strategic analysis of your specific threat landscape.
- Quantitative Analysis
- Threat Actors
- Money, Peoplepower, Time
- Attacker infrastructures
- MISP
- PyMISP
- Data visualisation
March 19, 2019 14:30-15:00
1430-Logistical-Budget-Leverett.pptx
MD5: 4129b30d77579665c35278c03f980237
Format: application/vnd.openxmlformats-officedocument.presentationml.presentation
Last Update: June 7th, 2024
Size: 1.31 Mb
- NL
Metrics and ATT&CK. Or how I failed to measure everything.
 Francesco BigarellaFrancesco Bigarella (ING Bank, NL)
Francesco BigarellaFrancesco Bigarella (ING Bank, NL)
Francesco is a threat intelligence analyst at ING Bank. He started as forensic analyst and soon transitioned to the intelligence world. While learning the craft, he has been looking into way to support the bank intelligence program and ended up being a firm promoter of the STIX framework. He holds a masters degree in computer science from the university Leiden.
Measuring the value of threat intelligence output isn't easy: How do we identify our intelligence gaps? Where should we focus our resources? Did it our intelligence output have an impact? Popular frameworks like ATT&CK can be used to establish standardized metrics to map to the intelligence cycle. Join me in exploring how the MITRE ATT&CK™ framework provides the building blocks to gain insights with a measurable business impact. And we will also explore how ATT&CK can be extended to provide insights outside its original scope. Because metrics can be fun!
March 20, 2019 10:00-10:30
- LU
MISP Threat Intelligence Analyst and Administrators
 Alexandre Dulaunoy
Alexandre Dulaunoy Andras IklodyAlexandre Dulaunoy (CIRCL, LU), Andras Iklody (CIRCL, LU)
Andras IklodyAlexandre Dulaunoy (CIRCL, LU), Andras Iklody (CIRCL, LU)
Alexandre Dulaunoy encountered his first computer in the eighties, and he disassembled it to know how the thing works. While pursuing his logical path towards information security and free software, he worked as senior security network consultant at different places (e.g. Ubizen, now Cybertrust). He co-founded a startup called Conostix, which specialised in information security management. For the past 6 years, he was the manager of global information security at SES, a leading international satellite operator. He is now working at CIRCL in the research and operational fields. He is also a lecturer in information security at Paul-Verlaine University in Metz and the University of Luxembourg. He is also the lead developer of various open source tools including cve-search and member of the MISP core team.
MISP is the leading open source platform to support threat intelligence sharing and management of information such as cyber security threats, financial fraud information, vulnerability information or even counter-terrorism related information.
The training session will help new and experienced users to understand and dive into the depths of the MISP platform and associated projects.
The session will include an overview on the usage of the MISP platform to support analysts, incident responders and security professionals in their day-to-day activities. In addition, a session of the training will cover the administration aspects aiming to help organisations to manage both internal or external sharing communities. During this one day training session, attendees will have the know-how needed to fully utilise and benefit from the majority of the features offered by the MISP platform.
Requirements for the training session:
For more information: https://www.circl.lu/services/misp-training-materials/
About the MISP project: https://www.misp-project.org - https://twitter.com/MISPProject
March 18, 2019 09:00-13:00, March 18, 2019 14:00-18:00
- US
OPSEC for investigators and researchers
 Krassimir Tzvetanov, PhDKrassimir Tzvetanov, PhD (Purdue University, US)
Krassimir Tzvetanov, PhDKrassimir Tzvetanov, PhD (Purdue University, US)
Krassimir Tzvetanov has worked for hardware vendors like Cisco and A10 focusing on threat research, DDoS mitigation features, product security and best security software development practices. Before joining Cisco, Krassimir was Dedicated Paranoid (security) at Yahoo!, Inc. where he focused on designing and securing the edge infrastructure of the production network. Part of his duties included dealing with DDoS and abuse. Before Yahoo! Krassimir worked at Google, Inc. as an SRE for two mission critical systems, the ads database supporting all incoming revenue from ads and the global authentication system which served all of the company applications.
Krassimir has established a couple of Threat Intelligence programs at past employers in the past and has been actively involved in the security community facilitating information exchange in large groups.
Currently Krassimir is a co-chair and co-founder of the FIRST CTI SIG.
Before retiring, he was a department lead for DefCon, and an organizer of the premier BayArea security event BayThreat. In the past he was also an organizer of DC650 - a local BayArea security meetup.
Krassimir holds Bachelors in Electrical Engineering (Communications) and Masters in Digital Forensics and Investigations.
Whether performing an in-depth investigation or merely quick research, the investigator (or researcher) and the investigation itself are exposed to certain risks.
This workshop focuses on security and safety issues pertaining to online research and investigations. It covers different areas of the investigative process and how tools and particular techniques can leak information detrimental to the case or the investigator.
Furthermore, it goes deeper into how investigators and blue teams can be profiled and targeted. Those can be either direct attack against their computer or supporting infrastructure, their person or the investigation, which in turn may be as subtle as steering the it in the wrong direction or making the evidence inadmissible in court.
More specifically the workshop will cover different browser and infrastructure fingerprinting techniques, browser hooking, instant message programs, email security and tracking.
As it covers the dangers, this workshop provides series of countermeasures and mitigations, which can help the investigator increase their level of safety and security and decrease their digital footprint.
Participants in the workshop will increase their awareness about what information they are disclosing and will find out new methods for augmenting their workflow to minimize exposure.
In addition, the workshop introduces containerization and how it can be used to segment and streamline the process.
Requirements: Students must bring: VMware Player or VirtualBox. (Note that the latter does not perform as well.)
March 18, 2019 09:00-13:00
- US
Quality Over Quantity: Determining Your CTI Detection Efficacy
 David J. BiancoDavid J. Bianco (SURGE / Cisco, US)
David J. BiancoDavid J. Bianco (SURGE / Cisco, US)
David has more than 20 years of experience in the information security field, with a particular focus on incident detection and response. He is active in the DFIR and Threat Hunting community, speaking and writing on the subjects of detection planning, threat intelligence and threat hunting. He is the principal contributor to The ThreatHunting Project (http://ThreatHunting.net). You can follow him on Twitter as @DavidJBianco or subscribe to his blog, "Enterprise Detection & Response" (http://detect-respond.blogspot.com).
You’ve collected a lot of IOCs, but is your Cyber Threat Intelligence (CTI) process serving you well? Quantity alone doesn’t tell the whole story. What kinds of intel are you collecting and how useful is it for identifying incidents? What are your strongest areas and where are your gaps? Do you know enough about your priority threats to feel confident in your detection stance against them? These are hard questions to answer, and there’s little existing guidance for answering them.
Taking a case study approach, this session will teach attendees how to use models such as the MITRE ATT&CK framework and the Pyramid of Pain to analyze and visualize the quality of their collected CTI information, not just it’s quantity.
Attendees will learn:
- How to load, normalize, and merge IOC data from disparate sources in your environment to make it ready for analysis
- How to enrich the data with information from the Pyramid of Pain and the ATT&CK framework
- How to visualize your collected threat intel to validate your collection strategy, to identify CTI strengths, and to prioritize closing collection gaps
- Why you should do these things on a regular basis
March 20, 2019 11:00-11:30
11-Quality-over-Quantity-Bianco.pptx
MD5: 63a06001c7a7edb36259c24e7e24c3ab
Format: application/vnd.openxmlformats-officedocument.presentationml.presentation
Last Update: June 7th, 2024
Size: 2.29 Mb
Reception sponsored by Digital Shadows
6 pm to 9:30 pm
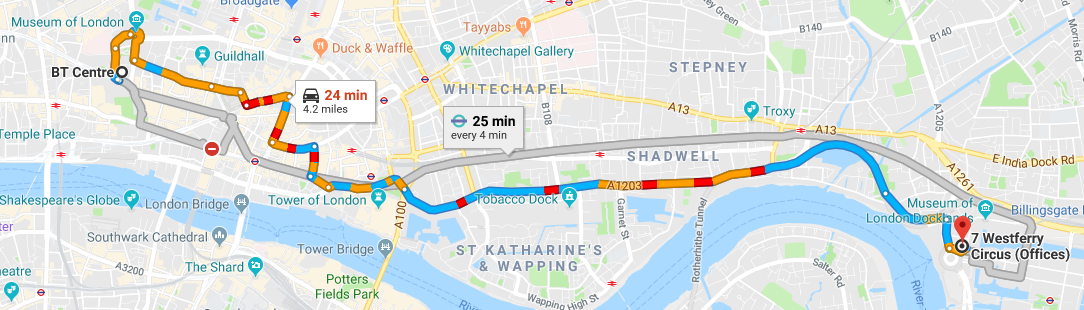
Digital Shadows
The Columbus Building
6th Floor, 7 Westferry Circus
London, E14 4HD
Hot food and drinks will be served
March 18, 2019 18:00-21:30
- PL
Semi-intelligence: trying to understand threats on a country level
Paweł Pawliński (CERT.PL, PL)
Paweł Pawliński is a principal specialist at CERT.PL. His past job experience include data analysis, threat tracking, and automation. He is responsible for the design and implementation of threat monitoring and data sharing systems. Paweł is an author of publications and training material that focus on the collection, analysis and exchange of information by CSIRTs.
When it comes to the effective use of intelligence, national CSIRTs have unique challenges. Leaving advanced targeted attacks aside, we are left with the task of protecting millions of users and companies facing a variety of threats to their data and money. Obviously threat intelligence plays an important role here but what impact can it make in practice?
Over the years we tried multiple approaches to collect relevant intelligence and to make it actionable. Looking back, we will try to identify some things that worked and ones that did not bring substantial results. The main topics will be automated monitoring, practical aspects of information exchange and situational awareness on a country level.
March 20, 2019 15:30-16:00
Social Event - Bounce on Old Street
March 19, 2019 19:00-22:00
- US
Statistical Techniques to detect Covert Channels Employing DNS
 Dhia Mahjoub
Dhia Mahjoub Thomas MathewDhia Mahjoub (Cisco Umbrella (OpenDNS), US), Thomas Mathew (Cisco Umbrella (OpenDNS), US)
Thomas MathewDhia Mahjoub (Cisco Umbrella (OpenDNS), US), Thomas Mathew (Cisco Umbrella (OpenDNS), US)
Dhia Mahjoub is the Head of Security Research at Cisco Umbrella (OpenDNS). He works with his team on building large scale threat detection and threat intelligence systems and driving new product features. Dhia has over 15 years experience in network security, has co-authored patents with OpenDNS and holds a PhD in graph data analysis. He regularly works with prospects and customers and speaks at conferences worldwide including Black Hat, Defcon, Virus Bulletin, FloCon, Infosecurity Europe, RSA, FS-ISAC, NCSC One Conference, RIPE conference, Hack in the Box, FIRST, and TF-CSIRT
Thomas Mathew is a Senior Security Researcher at Cisco Umbrella (OpenDNS) where he works on implementing pattern recognition algorithms to classify malware and botnets. His interest lies in using time series techniques on network sensor data to identify malicious threats. Previously, Thomas was a researcher at UC Santa Cruz, the US Naval Postgraduate School, and as a Product and Test Engineer at handsfree streaming video camera company Looxcie, Inc. He presented at Black Hat, Defcon, BruCon, FloCon, Kaspersky SAS, Infosecurity Europe, and O'Reilly Security
DNS tunneling has been rising in prominence over the last few years as a means for malware communication or data exfiltration.
Consequently - security operators are interested in identifying cases of DNS tunneling even if the tunneling is benign in nature.
The aim of this talk is to provide researchers with a detailed summary of the types of DNS tunneling we have identified in the wild as well as statistical techniques
to detect instances of DNS tunneling.
By modelling DNS tunneling as a communication process we hope to identify tunneling occurrences by similar statistical correlations across messages.
These correlations occur across multiple messages because the encoding process of a DNS tunneling protocol introduces either redundancies or similar lexical
patterns.
To prove this hypothesis we employ two different vector quantization schemes over different domain feature spaces to show that DNS tunneling domains cluster
together with higher frequency than ‘noise’ domains.
By analyzing the length structure of a domain’s labels we observe that tunneling domains follow a certain sequence length.
In addition, if we examine a feature space composed of the lexical structure of a domain label we also observe that DNS tunneling domains belonging to a similar
family cluster nearby.
Based on these two quantization schemes we build a DNS tunneling detector that can identify tunneling domains in the wild.
Key takeaways:
- The types/uses of DNS tunneling found in the wild
- Designing features to help identify DNS tunneling
- How to use machine learning models in conjunction with threat analysts to provide quick assessments of network threats
- The value of analyst feedback in the development cycle of automated models
- Categorizing types of DNS tunneling based on their structure
March 20, 2019 16:00-16:30
- US
The Hitchhiker's Guide to Threat Research
 Bryan LeeBryan Lee (Palo Alto Networks , US)
Bryan LeeBryan Lee (Palo Alto Networks , US)
Bryan Lee is a Principal Researcher with Unit 42 at Palo Alto Networks with a focus on espionage motivated adversaries. He has published extensive research into the Sofacy group in addition to discovering and (poorly) naming several other groups such as OilRig and DarkHydrus. Prior to joining Palo Alto Networks, Bryan spent nearly a decade at NASA working on projects in the advanced supercomputing division as well as the Security Operations Center. His diverse set of experiences provides a unique perspective of melding threat intelligence with security operations to provide actionable and operationally relevant research to the world.
DarkHydrus. OilRig. MagicHound. Ever wonder how Unit 42 or other research teams regularly produce threat intelligence and come up with those crazy names?
As an industry, we tend to revel in the mystique of threat intelligence, instead of readily explaining the mechanics of how we conduct our research. Continuous and active sharing of both threat data in addition to tracking and hunting techniques is absolutely pivotal to achieve positive outcomes as a community. Hiding behind the proverbial curtain and obfuscating the approaches of adversary tracking and hunting only benefits the adversaries. Though it may at times seem like voodoo, the truth is that the methodology for adversary tracking and hunting is actually not an overly complex task. Join Bryan in pulling the curtain back and learn about techniques and tools used on a daily basis for threat hunting and clustering. Understand how you can use the observed data points to generate actionable threat intelligence, enhancing your existing threat data as well as preparing for potential future threats.
Remember, don't panic, and always carry a towel.
March 19, 2019 15:30-16:00
1530-Hitchhikers-Guide-Lee.pptx
MD5: 32058875260003401bcc0f7d16bea891
Format: application/vnd.openxmlformats-officedocument.presentationml.presentation
Last Update: June 7th, 2024
Size: 8.24 Mb
- NL
TIBER: connecting threat intelligence and red teaming
 Marc Smeets
Marc Smeets Stan HegtMarc Smeets (Outflank, NL), Stan Hegt (Outflank, NL)
Stan HegtMarc Smeets (Outflank, NL), Stan Hegt (Outflank, NL)
Marc is a senior IT security specialist, red teamer and consultant. He started his professional IT security career in 2006. Prior to that he has worked in IT operations for 3 years. His main areas of expertise are adversary simulation/red teaming, network security, Windows and Active Directory security and detection of Blue Team activities.
Stan has more than a decade of experience in offensive security, with a strong focus on red teaming and attack simulations. His passion is to analyse and adopt the tradecraft of the bad guys in order to emulate their techniques in attack simulations for Outflank's clients. Stan loves developing malware for red teaming purposes (WinAPI <3) and exploring opportunities for abuse in Windows components such as MS Office, COM, .NET and PowerShell.
TIBER (Threat Intelligence Based Ethical Red Teaming) is a framework that aims to deliver attack simulations of the highest quality in order to test the financial sector’s resilience to cyber attacks. Since May 2018, it is accepted by the European Central Bank as the go-to cyber resilience testing framework for national and European authorities within the Euro zone. The framework has big aspirations, including the ambition to test TTPs employed by nation state actors in operations that run for multiple months. But is this even possible, and how?
In this talk we will deep dive into the TIBER framework and our hands-on experiences with it, sharing best practices on how to connect threat intelligence with red teaming. Amongst others, the following topics will be addressed:
- How is TIBER different from other red teaming and threat intelligence frameworks (such as CBEST)?
- What threat intelligence does a red team need to perform a top notch test?
- Threat actor modelling in red teaming.
- Common OPSEC mistakes by blue teams during operational TI collection.
- RedELK: open source tooling for offensive TI during red teams operations.
March 19, 2019 11:15-12:00
- NO
 Dr. Martin EianDr. Martin Eian (mnemonic, NO)
Dr. Martin EianDr. Martin Eian (mnemonic, NO)
Dr. Martin Eian is the Head of Research at mnemonic, and he is the Project Manager for the research projects "Semi-Automated Cyber Threat Intelligence (ACT)" and "Threat Ontologies for CyberSecurity Analytics (TOCSA)". He has more than 15 years of work experience in IT security, IT operations, and information security research roles. In addition to his position at mnemonic, he is a member of the Europol EC3 Advisory Group on Internet Security.
The ACT platform is an open source, scalable graph database with support for granular access control and workflow management. ACT enables advanced threat enrichment, threat analysis, visualization, process automation, information sharing, and powerful graph analytics. Its modular design and APIs facilitate implementing new workers for enrichment, analysis, information sharing, and countermeasures.
Key takeaways for the ACT workshop participants:
- The ACT platform design and technical implementation choices
- Analysis techniques using simple queries and graph interaction (drill-down, filtering, layouts)
- Advanced analysis using graph queries
The ACT platform source code is available on Github: https://github.com/mnemonic-no
A read-only platform instance pre-loaded with OSINT is available on AWS:
https://act-eu1.mnemonic.no
https://act-eu1.mnemonic.no/examples/
March 18, 2019 14:00-18:00
- US
Turning intelligence into action with MITRE ATT&CK™
 Adam Pennington
Adam Pennington Katie NickelsAdam Pennington (MITRE, US), Katie Nickels (MITRE, US)
Katie NickelsAdam Pennington (MITRE, US), Katie Nickels (MITRE, US)
Katie Nickels is the ATT&CK Threat Intelligence Lead at The MITRE Corporation, where she focuses on applying cyber threat intelligence to ATT&CK and sharing why that’s useful. She has worked in Security Operations Centers and cyber threat intelligence for nearly a decade, hailing from a liberal arts background with degrees from Smith College and Georgetown University. Katie has shared her expertise with presentations at BSides LV, the FIRST CTI Symposium, and multiple SANS Summits. Katie is a Teaching Assistant for the SANS FOR578: Cyber Threat Intelligence course and was a member of the 2019 SANS CTI Summit Advisory Board. She was the 2018 recipient of the President's Award from the Women's Society of Cyberjutsu. Katie is also the Program Manager for the Cyberjutsu Girls Academy.
Adam Pennington (@_whatshisface), Principal Cyber Security Engineer, MITRE Adam Pennington is a member of the core ATT&CK team, and collected much of the intelligence leveraged in creating its initial techniques. He has spent much of his 10 years with MITRE studying and preaching the use of deception for intelligence gathering. Prior to joining MITRE, Adam was a researcher at Carnegie Mellon's Parallel Data Lab and earned his BS and MS degrees in Computer Science and Electrical and Computer Engineering as well as the 2017 Alumni Service Award from Carnegie Mellon University. Adam has published in a number of venues including USENIX Security and ACM Transactions on Information and System Security.
Many of you have embraced the concept of a threat-informed defense but are still struggling to bridge the gap between intelligence and action. MITRE ATT&CK provides a structure for organizing adversary tactics, techniques, and procedures (TTPs) that allows intel analysts to organize adversary behaviors and communicate them in a way that is actionable by defenders. The presenters will explain how they recommend you use ATT&CK to improve the practice of threat intelligence based on experience gained mapping hundreds of reports to ATT&CK over a five-year period. The presenters will also explore some of the biases and limitations of using ATT&CK for threat intelligence, how to avoid traps that you may encounter as a result, and ways that intelligence expressed with ATT&CK can be successfully applied to defend against your priority threats.
March 20, 2019 09:00-09:30
Tutorial on OSINT tradecraft
Larry Leibrock (DA and Ph.D.)
This fast-paced tutorial offers a grounded introduction to the open-source intelligence discipline, (OSINT), theory, practices, checklists, and tradecraft focused on cyber-threat environments. This workshop will make use of curated set of tools and frameworks engaging students acting as intelligence analysts examining, discussing, and analyzing the aspects of OSINT, which is a relatively new and emerging intelligence discipline.
Participants should bring personal computers (with admin privileges) with wireless networking enabled to make use of a VM image with case materials and tools for use in the tutorial. There
will be a DVD/USB boot image of the required CTI software provided prior to the workshops. Participants need a familiarity with Windows and Linux Shells and VM operations – a wireless access point will be provided for tool and evidentiary downloads
March 18, 2019 14:00-18:00
- US
Using ATT&CK™ for Cyber Threat Intelligence Workshop
 Adam Pennington
Adam Pennington Katie Nickels
Katie Nickels Richard StruseAdam Pennington (MITRE, US), Katie Nickels (MITRE, US), Richard Struse (MITRE, US)
Richard StruseAdam Pennington (MITRE, US), Katie Nickels (MITRE, US), Richard Struse (MITRE, US)
Adam Pennington (@_whatshisface), Principal Cyber Security Engineer, MITRE
Adam Pennington is a member of the core ATT&CK team, and collected much of the intelligence leveraged in creating its initial techniques. He has spent much of his 10 years with MITRE studying and preaching the use of deception for intelligence gathering. Prior to joining MITRE, Adam was a researcher at Carnegie Mellon's Parallel Data Lab and earned his BS and MS degrees in Computer Science and Electrical and Computer Engineering as well as the 2017 Alumni Service Award from Carnegie Mellon University. Adam has published in a number of venues including USENIX Security and ACM Transactions on Information and System Security.
Katie Nickels is the ATT&CK Threat Intelligence Lead at The MITRE Corporation, where she focuses on applying cyber threat intelligence to ATT&CK and sharing why that’s useful. She has worked in Security Operations Centers and cyber threat intelligence for nearly a decade, hailing from a liberal arts background with degrees from Smith College and Georgetown University. Katie has shared her expertise with presentations at BSides LV, the FIRST CTI Symposium, and multiple SANS Summits. Katie is a Teaching Assistant for the SANS FOR578: Cyber Threat Intelligence course and was a member of the 2019 SANS CTI Summit Advisory Board. She was the 2018 recipient of the President's Award from the Women's Society of Cyberjutsu. Katie is also the Program Manager for the Cyberjutsu Girls Academy.
Richard Struse is the Chief Strategist for Cyber Threat Intelligence (CTI) at The MITRE Corporation, leading the effort to improve cyber defense by better understanding the adversary’s tactics and techniques. In addition, he is the chair of the Cyber Threat Intelligence Technical Committee within OASIS, an international standards development organization. In 2018, Mr. Struse was elected to serve on the board of directors of OASIS. Previously, Mr. Struse served as the Chief Advanced Technology Officer for the U.S. Department of Homeland Security’s National Cybersecurity and Communications Integration Center (NCCIC) where he was responsible for technology vision, strategy and implementation in support of the NCCIC’s mission. Mr. Struse is the creator of the STIX and TAXII automated information sharing initiatives which have been widely adopted across the public and private sectors. In October 2014, Secretary of Homeland Security Jeh Johnson presented Mr. Struse with one of the department’s highest honors, the Secretary’s Award for Excellence, in recognition of his pioneering work on STIX and TAXII. Prior to joining DHS, Mr. Struse was Vice President of Research and Development at VOXEM, Inc., where he was responsible for the architecture, design and development of a high-performance, extreme high- reliability communications software platform that is in use in telecommunications systems around the world. He began his technical career at Bell Laboratories where his work focused on tools to automate software development and the UNIX operating system. In 2015 Mr. Struse was named by Federal Computer Week as one of the “Federal 100” in recognition of his leadership role in the development of cyber threat intelligence technology standards. In 2016, OASIS selected Mr. Struse to receive their “Distinguished Contributor” award for his work as “a pioneer in the development of the STIX, TAXII, and CybOX standards and was instrumental in successfully transitioning the CTI work to OASIS.”
Learn how to apply ATT&CK to improve your threat intel practices from the MITRE ATT&CK team. This workshop will teach you how to map threat reporting into ATT&CK techniques and transform the resulting intelligence into specific defensive measures. Through a series of presentations and exercises, you will gain hands-on experience identifying attacker behaviors in intelligence reporting, analyzing those behaviors leveraging ATT&CK and open source tools, and translating it into specific defensive recommendations.
**Requirements: Students must bring a laptop capable of connecting to symposium WiFi. The laptop must have a web browser as well as a PDF reader.
March 18, 2019 09:00-13:00
- CH
Your Requirements are not my Requirements
 Pasquale StirparoPasquale Stirparo (Google, CH)
Pasquale StirparoPasquale Stirparo (Google, CH)
Pasquale Stirparo is currently working as Incident Manager at Google. Prior to this, he worked as part of the Digital Forensics, Incident Response and Threat Intelligence teams in the Financial sector, the Joint Research Centre (JRC) of European Commission and at consulting firms. In 2016 he was appointed at the Advisory Group on Internet Security at the European Cyber Crime Center (EC3) of Europol and he is currently Incident Handler with the SANS Internet Storm Center (ISC). Pasquale has also been involved in the development of the Digital Forensics standard “ISO/IEC 27037: Guidelines for identification, collection and/or acquisition and preservation of digital evidence”, for which he led the WG ISO27037 for the Italian National Body in 2010. Pasquale holds a Ph.D. in Computer Security from the Royal Institute of Technology (KTH) of Stockholm and a M.Sc. in Computer Engineering from Polytechnic of Torino, and is certified GCFA, GREM, OPST, OWSE, ECCE. He is also the co-author of the book “Learning iOS Forensics” edited by PacktPub, awarded as "Best Forensics Book of the Year 2015" by Forensics 4:cast Awards.
One would expect setting up the requirements to be the first task completed before investing time in researching and collecting any type of intelligence. However, intelligence requirements are still too often overlooked and organisations jump immediately to the collection phase which, sadly, often translates into buying and ingesting as many feeds as possible, everybody looking for “APTs”. The main goal of properly setting the requirements is to understand which type of information is of primary interest for your organization, and be sure that the most relevant and critical one is processed and not lost into the noise.
In this talk, we will give the audience an understanding of what “intelligence requirements” really are and why they are such an important component of the intelligence cycle. Finally, we will give initial practical guidelines on how to start setting up and defining them.
March 20, 2019 14:30-15:00